How hackers crack passwords and why you can’t stop them
Experts agree that it’s long past time for companies to stop relying on traditional passwords. They should switch to more secure access methods like multi-factor…
What is the cyber kill chain? Why it’s not always the right approach to cyber attacks
As an infosec professional, you’ve likely heard about using a cyber kill chain, also known as a cyber attack lifecycle, to help identify and prevent…
How AI can help you stay ahead of cybersecurity threats
Since the 2013 Target breach, it’s been clear that companies need to respond better to security alerts even as volumes have gone up. With this…
Unlimited DDoS protection the new norm after Cloudflare announcement
Late last month, global distributed denial of service (DDoS) protection provider Cloudflare announced that it would no longer charge customers extra when they were under…
Shadow cloud apps pose unseen risks
It happens in every company. Employees find a cool new online service that makes them more productive. They create free or low-cost accounts on devices…
The best enterprise antivirus: Kaspersky leads in latest tests
Ransomware and other threats often get through signature-based antivirus protection, giving it a bad rap. However, anti-virus tools still play an important role in the…
What is a fileless attack? How hackers invade systems without installing software
“We see it every day,” says Steven Lentz, CSO at Samsung Research America. “Something coming through, some exploit type, unknown ransomware. We’ve stopped several things…
Is universal end-to-end encrypted email possible (or even desirable)?
People expect their email to be private between them and the recipient, but in reality, the contents of your email are exposed during transmission. Full…
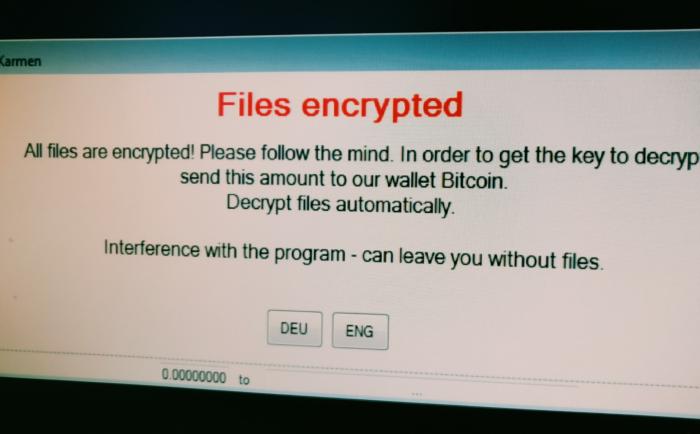
What’s new in ransomware?
In June, South Korean hosting company Internet Nayana, Inc., was hit by a ransomware attack that took down its 153 Linux web servers — home…
Look beyond job boards to fill cybersecurity jobs
The cybersecurity talent shortage keeps getting worse. According to Cybersecurity Ventures, the cost of cybercrime will double from $3 trillion globally in 2015 to $6…
Is your data being sold on the dark web?
Sonatype’s crown jewel is its database of descriptions of over 1.2 million open source packages. “If that is lost, it could be an existential outcome,”…
Two years after the OPM data breach: What government agencies must do now
The Office of Personnel Management breach in June 2015 was a big wake up call to our federal government, and, in its wake, a number…
With new dynamic capabilities, will whitelisting finally catch on?
Everybody knows and hates whitelisting. Employees are only allowed to install approved software on their desktops and laptops, so they’re always complaining and asking for…
Few firms will be ready for new European breach disclosure rules, fines
The new European General Data Protection Regulation goes into effect next May, with onerous notification requirements and high penalties, but a year might not be…
APT3 hackers linked to Chinese intelligence
The APT3 hacker group, which has been attacking government and defense industry targets since 2010, has been linked to the Chinese Ministry of State Security,…
Few firms will be ready for new European breach disclosure rules, fines
The new European General Data Protection Regulation goes into effect next May, with onerous notification requirements and high penalties, but a year might not be…
APT3 hackers linked to Chinese intelligence
The APT3 hacker group, which has been attacking government and defense industry targets since 2010, has been linked to the Chinese Ministry of State Security,…
Be wary of fake WannaCry fixes
When the WannaCry malware hit, many users were scrambling for fixes — but some of the proffered solutions were actually just more malware, in disguise.…
Suffolk County greets hurricane season with updated alerting system
Last September, as the East Coast prepared for Tropical Storm Hermine, the emergency broadcasting system accidentally sent out an evacuation alert for all of Long…
WannaCry fallout — the worst is yet to come, experts say
The massive scale of the recent WannaCry ransomware attack has exposed some significant weaknesses in global IT systems, and we’re likely to see more attacks…
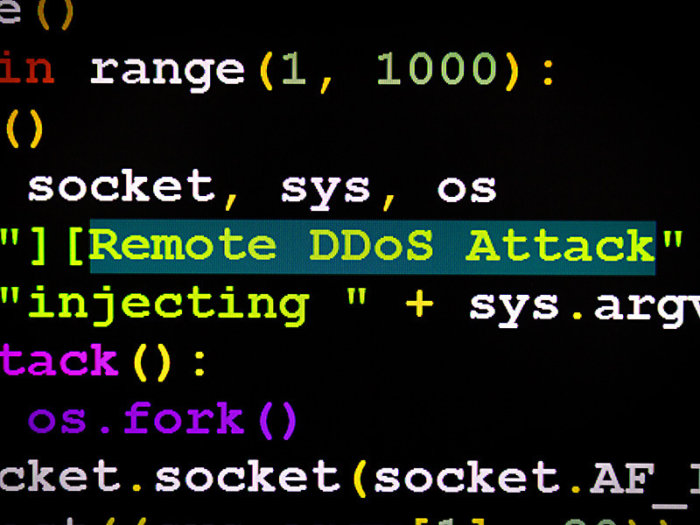
Cybercrooks fight over DDoS attack resources
As more groups get into the denial-of-service attack business they’re starting to get in each other’s way, according to a report released this morning. That…
Ad network takes steps to reduce fraud
The fraud rates for online ads are scary, with advertisers losing billions of dollars each year.Last week, Pixalate released a report showing that 35 percent…
Report: Average ransomware demand now over $1,000
The average amount of a ransomware demand has increased from $294 in 2015 to $1,077 last year, according to a report released last week by…
Criminals turning to fraudulent gift cards
As retailers and other businesses increase security measures to prevent the use of gift cards purchased with stolen credit card numbers, cyber criminals have been…
Automated mitigation on endpoint devices and networks can be tricky
Many companies have automated systems in place for preventing, detecting, and investigating security incidents, but automating the incident response and mitigation process for networks and…
Security automation is maturing, but many firms not ready for adoption
The security automation industry is still in its infancy, with most vendors just a year or two old, but there are already some promising technologies…
How the insurance industry could change the game for security
The recent growth in the cyber insurance market is already improving cybersecurity in some industry segments, and has the potential to do more — if…
Latest OWASP Top 10 looks at APIs, web apps
The new release of the OWASP Top 10 list is out for public comment from the Open Web Application Security Project, and while most of…
Cyberespionage, ransomware big gainers in new Verizon breach report
Verizon released its tenth annual breach report this morning, and cyberespionage and ransomware were the big gainers in 2016.Cyberspionage accounted for 21 percent of cases…
Cybersecurity industry braces for tighter visa rules
Email authentication company ValiMail just got done with the process of bringing in a new employee under the H-1B visa program, which allows companies to…