5 non-traditional hiring tips for InfoSec
There’s a dramatic shortage of qualified information security professionals in the industry today. Globally, we’re a million people short, according to Cisco’s 2014 Annual Security…
Tools catch security holes in open source code
This year has been the best of times and the worst of times for open source code and security. On the one hand, the latest…
10 tips to attract women to infosec jobs
Women make up just 11 percent of information security professionals. Just increasing that number to 22 percent would solve the industry’s staffing shortage problem. Unfortunately,…
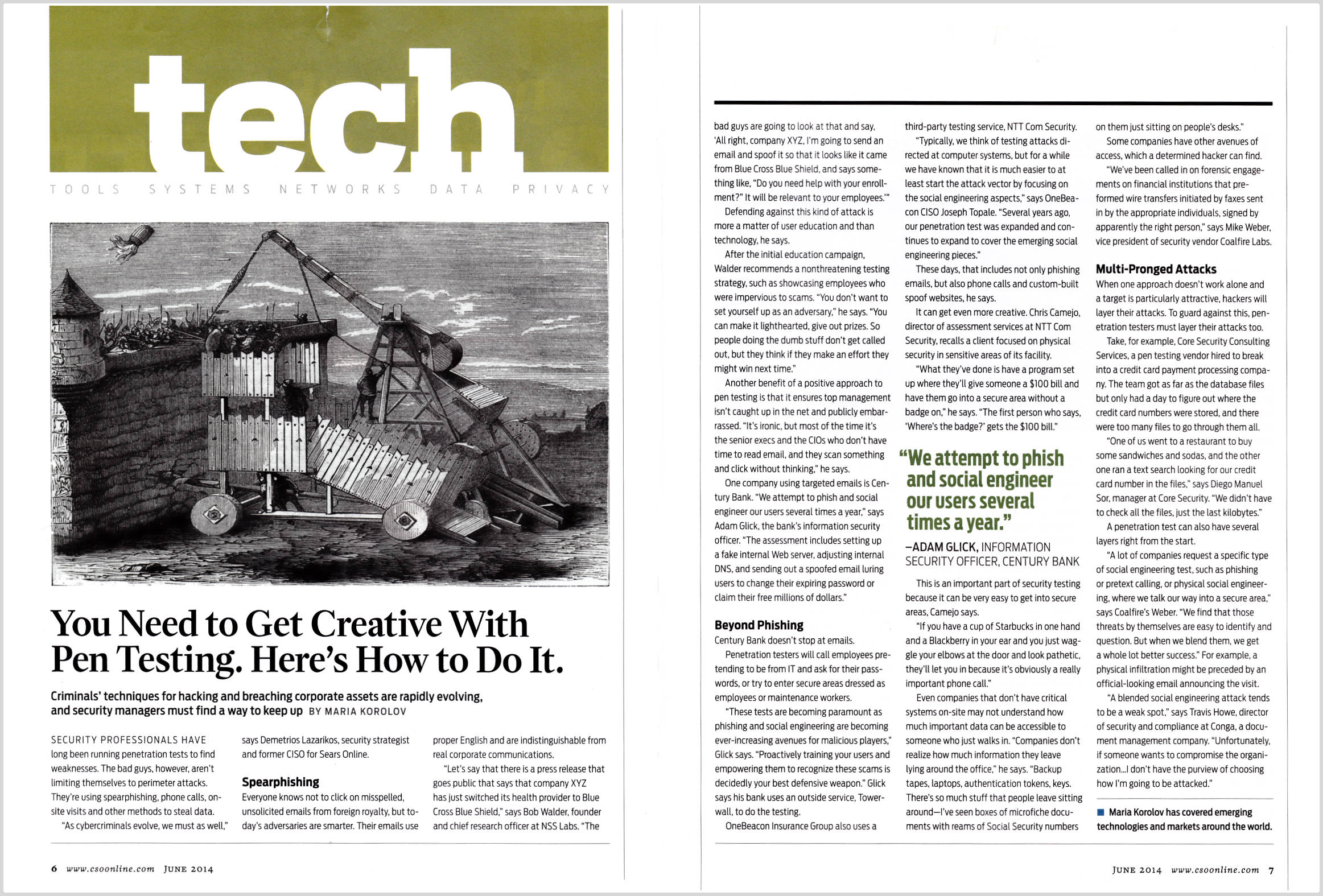
How to get creative with your penetration testing
While there are plenty of standardized methods for penetration testing that we’re all familiar with, the bad guys aren’t sticking to traditional methods for…
You Need to Get Creative With Pen Testing. Here’s How to Do It.
Security professionals have long been running penetration tests against their firewalls and other security systems to find weaknesses that need to be addressed. The Common…
Forgotten risks hide in legacy systems
Cover story These days, there’s no shortage of new business technologies and new threat vectors to the enterprise. But what many companies forget is that…
Info sec industry still struggles to attract women
Even as women have made dramatic advances in medicine, law, and other fields, the proportion of women pursuing undergraduate degrees in the computer sciences has…
10 reasons to take a Chromebook on the road
If you’re trying to decide which device to buy for your next trip because your current laptop is too old, too slow, too heavy and…
SaaS vendors, customers, finding new ways to secure the cloud
Rogue employees, hackers, government employees all threats to keeping information stored on the cloud private Edward Snowden’s leaks about NSA spying may have brought the…
Bitcoin: Seven reasons to be wary
Of all the virtual currencies out there, BitCoin is the most interesting from a technical perspective – and the least interesting from the business point…
How to Survive a Cloud Outage
Amazon’s infamous cloud outage in April brought down a number of popular Web sites, including foursquare and Reddit – but many of Amazon’s enterprise cloud…
Five iPad Safety Tips
1. Encrypt, encrypt, encrypt. There are two parts to the data encryption challenge – encrypting stored data, and encrypting data that’s moving over public networks,…